You may not be aware of it, but you were using two-factor authentication (2FA) before it became widespread in protecting online accounts. Just think about the moment you withdraw cash from an ATM: you have the physical card, but you still need to know the PIN.
In fact, 2FA is recommended to anyone protecting highly sensitive data, but apparently, even some of the biggest companies don't implement it, which leaves them vulnerable to hacker attacks. The use of 2FA would have prevented high profile data breaches such as that of Deloitte, one of the big four accountancy companies worldwide, for example.
The Second Layer of Security
 If all that is needed to sign into an account is your email address or username and a password, then this is single factor authentication. The secondary layer steps into the picture to augment what you know with “something you have”. However, there are two approaches to this layer of security: two-step verification and two-factor authentication. This second layer has created confusion in the media, which fits well for those who want to obfuscate the difference between the two methods.
If all that is needed to sign into an account is your email address or username and a password, then this is single factor authentication. The secondary layer steps into the picture to augment what you know with “something you have”. However, there are two approaches to this layer of security: two-step verification and two-factor authentication. This second layer has created confusion in the media, which fits well for those who want to obfuscate the difference between the two methods.
The Difference Between Two-Step Verification and Two-Factor Authentication
It's important to highlight that there is a significant difference between two-step verification and two-factor authentication, and that they are not interchangeable, as is often stated in media reports.
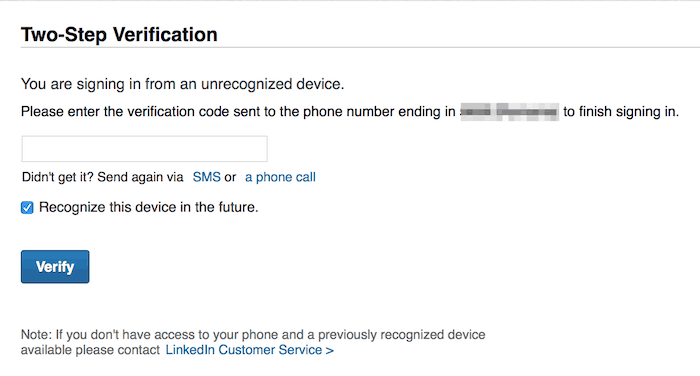
A second layer in the authentication process means there will be two steps involved, requiring a numeric code sent via text message to the account owner’s preset phone number, a hardware token issued by a company’s IT department that generates a number to enter upon logging in or even a smartphone app that produces a similar function.
Only the hardware token and a trusted device fit into the category of 2FA, since this method refers exclusively to authentication mechanisms where the two authentication elements combine two mutually exclusive means of access.
For example, the popular Google Authenticator app and third party solution Authy are used by multiple service providers since these services generate a one-time numeric code valid only for the 30 seconds that a user needs to insert into the required field to log into their account.
But these aren’t really 2FA because the secondary key to authentication is on the device itself; that information is generated remotely and can be stolen by an attacker. A good example of this security flaw can be seen in the way LastPass implemented code generation for the two-step verification. Discovered in early 2017, LastPass used a QR code to generate a code for the second step, but this info was stored in a URL that attackers could obtain from the password itself, making the whole point of the second step obsolete.
The same goes for the two-step verification process using SMS. Hackers have various ways to steal text messages sent through the carrier, thanks to the vulnerabilities of the telecommunication companies and the process of getting a new SIM card with the same number.
Two-factor authentication combines two elements: ‘something you know’ (the password) or ‘something you are’ (biometrics) with ‘something you have’, which can be a trusted device. Apple customers, for example, can set up different devices running iOS 9 or later, macOS El Capitan 10.11 or later, Windows PC with iCloud for Windows 5 and iTunes 12.3.3 and later to receive temporary codes. If the trusted device is offline, it will act as a hardware token, as you can still get a verification code.
How Could 2FA Have Prevented the Deloitte Hack?
 The Guardian's reporting, the hackers gained “access to usernames, passwords, IP addresses, architectural diagrams for businesses and health information. Some emails had attachments with sensitive security and design details.” The administrator account was only protected by single-factor authentication, aka username and password. With 2FA enabled, the system would have immediately sent a requirement to the admin account owner to enter the numeric code sent to their trusted device and therefore preventing any outside access, since physical access to the device would have been required – therefore totally blocking the hacker’s progress.
The Guardian's reporting, the hackers gained “access to usernames, passwords, IP addresses, architectural diagrams for businesses and health information. Some emails had attachments with sensitive security and design details.” The administrator account was only protected by single-factor authentication, aka username and password. With 2FA enabled, the system would have immediately sent a requirement to the admin account owner to enter the numeric code sent to their trusted device and therefore preventing any outside access, since physical access to the device would have been required – therefore totally blocking the hacker’s progress.
Best Password Managers of 2024
| Rank | Provider | Info | Visit |
1
|
Editor's Choice 2024
|
|
|
2
|
 |
|
|
|
3
|
|
Get the Best Deals on Password Managers
Subscribe to our monthly newsletter to get the best deals, free trials and discounts on password managers.



Share Your Comment