Humans are considered the weakest link when it comes to data security – and there’s a solid reason for this. Many people still underestimate the ease with which hackers can crack weak passwords, putting sensitive information at risk. It is vital to understand the importance of having a strong password and how to avoid mistakes that can lead to threats and breaches.
Humans are considered the weakest link when it comes to data security – and there’s a solid reason for this. Many people still underestimate the ease with which hackers can crack weak passwords, putting sensitive information at risk. It is vital to understand the importance of having a strong password and how to avoid mistakes that can lead to threats and breaches.
How Long Does It Take to Crack a Password?
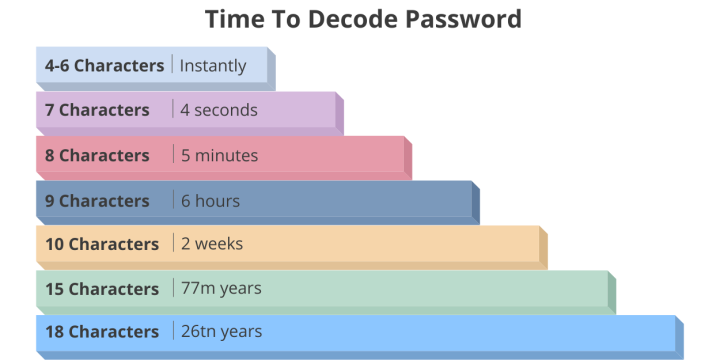
When it comes to password cracking, time is of the essence. The length of time it takes for a hacker to crack a password depends on several factors, such as its complexity and size. For instance, a weak password can be deciphered within seconds, while a strong and lengthy password can increase the time required to reveal it. In the end, having a strong password is the key to being safe online.
Hive Systems calculated the approximate time for a password to be decoded using cloud and AI software based on the number of characters:
What Is Password Cracking?
Password cracking is an attack vector that involves hackers attempting to crack or determine a password. If you’re wondering what a password-cracking attack looks like, here is the general process that a hacker follows to decode passwords:
- Gain access to an encrypted password via illegal means.
- Choose a cracking technique, such as brute-force or dictionary attacks.
- Select a cracking tool.
- Run the cracking tool.
Password Hacking Techniques: Offline vs Online Attacks
Password cracking techniques can be broadly categorized into two types: offline and online attacks. Online attacks occur in real time and target a live host or system by employing brute-force or wordlist attacks against login forms, sessions, or other authentication methods. These attacks are executed directly on the system being targeted.
On the other hand, offline attacks involve extracting password hashes stored by the victim, attempting to crack them without alerting the targeted host. Offline attacks are more prevalent due to their effectiveness. Since they exploit security vulnerabilities in the victim’s infrastructure, they allow hackers to obtain the necessary information to crack the passwords at their own convenience.

Types of Password Cracking Techniques
While online attacks focus on immediate exploitation, offline attacks provide hackers with the opportunity to perform extensive analysis and employ advanced techniques to crack passwords without raising suspicion. It’s important to understand the different approaches in order to implement the appropriate security measures. The most used attack techniques are:
- Brute-force attacks
- Dictionary attacks
- Phishing
- Rainbow table attacks
- Credential stuffing
- Social engineering
Brute-Force Attacks
One of the most popular cracking techniques for passwords of up to eight characters is the brute-force attack. This technique follows a systematic approach, as the hacker diligently tests every possible combination of letters, numbers, and punctuation marks. Each combination is then converted into a hash and compared with the target password’s hash.

The success of brute-force attacks depends on the length of the password. As the password grows longer, the brute-force method becomes increasingly time-consuming, ranging from minutes to potentially several years.
Dictionary Attacks
In the context of cybersecurity, dictionary attacks stand as a close cousin to the brute-force attack, yet with a distinctive approach.
Instead of methodically trying every possible character combination, the hacker takes advantage of a pre-compiled list of likely matches, such as common English words. These lists, employed by dictionary attack tools, encompass familiar passwords, excerpts from literary works, and other predictable combinations.

Phishing
Phishing poses a serious threat to password security nowadays. With cunning precision, cybercriminals masquerade as reputable organizations or trusted individuals, using deceptive emails, messages, and websites to trick their targets.
This practice preys on human vulnerability and trust, emphasizing the need for users to stay on guard and take proactive protective measures. Verifying the authenticity of communication channels and staying informed about the latest techniques is vital for safeguarding passwords from falling into the wrong hands.
Rainbow Table Attacks
Rainbow table attacks capitalize on pre-computed lookup tables brimming with an extensive array of password hashes and their corresponding plaintext counterparts. By comparing the targeted password hashes with the entries meticulously stored within the rainbow table, attackers gain a fast path to retrieving the original password.
While the initial creation of the tables can be a time-consuming task, once they’re generated, the attack itself becomes much faster.
Credential Stuffing
Credential stuffing hinges on the fact that many individuals rely on the same login credentials across different websites and platforms. Taking advantage of this habit, hackers employ automated tools to methodically plug stolen usernames and passwords into various online services. Their aim is to exploit those who reuse passwords.
Once the code is cracked, the consequences can be dire for the compromised accounts, potentially leading to data breaches, identity theft, or financial fraud.

Social Engineering
Social engineering involves the art of psychological manipulation and deceit. Through phone calls, emails, or face-to-face encounters, attackers aim to trick their victims into revealing sensitive information, downloading malware, or granting unauthorized access to the cybercriminal.
By gathering intelligence about their targets, hackers use various communication channels to perpetrate their scams and achieve their goals. The success of social engineering relies on the ability to exploit people’s trust, making it crucial for everyone to stay vigilant and cautious while interacting online.
Most Common Password Cracking Tools Used by Hackers
Passwords are cracked using various methods and attacking tools. Below are the five most used tools:
- Hashcat: Supporting over 300 types of hashes, this software takes password cracking to a whole new level. With its highly coordinated processing, Hashcat can crack multiple passwords simultaneously on multiple devices, supporting distributed hash-cracking systems.
- Brutus: This tool is one of the most used online password cracking tools. With a focus on speed and flexibility, it’s the top choice among hackers looking to crack passwords in record time.
- John the Ripper: Open-source software that’s able to detect password hash types automatically. It can also run a wide variety of attacks, increasing its popularity amongst hackers.
- THC Hydra: This online password-cracking powerhouse is all about brute-force guessing attacks. It relentlessly tries different combinations to determine user credentials and gain access to secured accounts.
- RainbowCrack: This tool specializes in using rainbow tables. With it, it’s possible to generate custom rainbow tables or utilize existing ones that are available for download.

How To Secure Your Passwords
In a world of fast-evolving cyberthreats, safeguarding your digital presence starts with using strong and unique passwords for each account. However, the real challenge boils down to where and how you manage and store these passwords securely.
This is where reputable password management tools like Keeper, which provide a convenient and secure solution, come into play. These platforms generate and store complex passwords, alleviating the burden of memorization or risky notetaking. However, storing passwords is not everything password managers can do. They’re also excellent at eliminating weak passwords, monitoring the dark web, simplifying password management, and making it straightforward to log into accounts.
Regularly updating and changing passwords is also vital for staying one step ahead of potential breaches. To guarantee password security, it’s recommended to switch passwords every three to six months.
Furthermore, staying vigilant about phishing attacks and keeping your software and devices updated also play a huge part in maintaining password security. Keeping bugs at bay and continuing to be informed are important steps to keep you safe online.
With the right precautions and software, you can navigate the digital landscape with confidence. Creating a safer environment for yourself and the people around you is easy – it can be achieved by simply adopting these practices and embracing the advancements in password safety.
Best Password Managers of 2024
| Rank | Provider | Info | Visit |
1
|
Editor's Choice 2024
|
|
|
2
|
 |
|
|
|
3
|
|
Get the Best Deals on Password Managers
Subscribe to our monthly newsletter to get the best deals, free trials and discounts on password managers.